AP Exam Study Blog
Beneficial and Harmful Effects of Computing
Beneficial Effects:
Harmful Effects:
Digital Divide
Causes:
Consequences:
Possible Solutions:
Computing Bias
Examples:
Causes
Solutions:
Crowdsourcing
Examples:
Advantages:
Disadvantages:
Legal and Ethical Concerns
Legal Issues:
Ethical Issues:
Safe Computing
Binary Search Algorithm
Purpose:
Steps:
Efficiency:
Lists and Filtering Algorithms
Lists:
Filtering:
Common Uses:
Simulation/Games and Random Algorithms
Simulation:
Games:
Random Algorithms:
Big O & Algorithm Efficiency
Common Big O Types:
MCQ Reflection
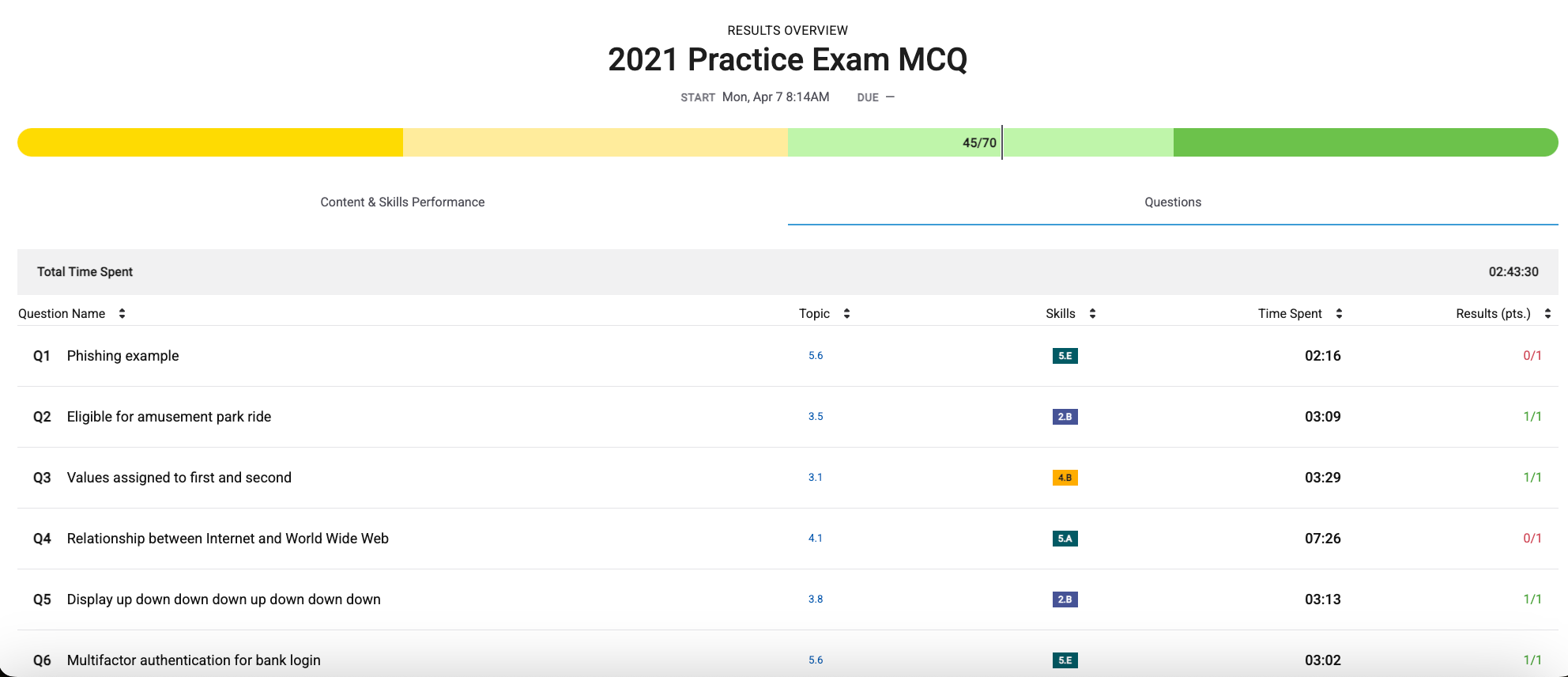
Overall Score: 45/70
1. (D): Phishing is a technique that attempts to trick a user into providing personal information. In this case, the user is tricked by a fraudulent e-mail.
4. (D): The Internet is the global system of interconnected computer networks that uses protocols to connect devices worldwide. The World Wide Web is an information system (of pages, programs, and files) that is accessible over the Internet.
14. (C) As is, the procedure traverses numberList from left to right and returns true whenever it encounters a value that is less than the preceding value. If it never encounters such a value, false is returned.
16. (B) A no-rights-reserved Creative Commons license is used when the creator of a published work wants the work to be made freely available to everyone.
19. (D) A strong password is something that is easy for a user to remember but would be difficult for someone else to guess based on knowledge of that user. Weak passwords can often be guessed based on publicly available information about a user.
26. (A) The efficiency of a parallel computing solution is limited by the sequential portion of the solution. If each step is dependent on the preceding step, then each step must wait for the previous step to complete before executing. Therefore, the solution is completely sequential and does not benefit from parallel computing.
32 (A) Public-key encryption is considered a secure way of encoding data to prevent unauthorized access.
41. (A) Crowdsourcing is the practice of using input or information obtained from a large number of people via the Internet. In this case, input on a player is provided by other players of the game.
43. (A) Keylogging is the use of a program to record every keystroke made by a computer to gain fraudulent access to passwords and other confidential information.
50. (A) Symmetric encryption uses a single key for both encryption and decryption of data. Since the key can be used to unlock the data, it should be kept secret.
53. (A) Step 4 checks every element of the list, incrementing count each time target appears. Step 5 prints true if and only if count appears multiple times in the list.
55. (C) This code segment assigns the value of the last element of the list to the variable temp, then removes the last element of the list, then inserts temp as the first element of the list.
63. (A) and (D) When input1 and input2 are both true, the expression (input1 AND input2) is true, so NOT (input1 AND input2) will evaluate to false. In all other cases, (input1 AND input2) will evaluate to false, so NOT (input1 AND input2) will evaluate to true.
64. (B) and (C) This line should be removed. This statement causes result to be assigned the value "adult", even if it should have been assigned the value "senior citizen".
70. (A) and (C) This code segment assigns the characters to the left of position n to newStr. The code segment then concatenates newStr with the substring consisting of the characters to the right of position n.
MCQ Topics I need to focus on

4.1 The internet
Packet: a small amount of data sent over a network. Each packet includes the source and the destination information.
Packet switching: the message (file) is broken up into packets and sent in any order. The packets are reassembled by the recipient’s device
Path: a path between two computing devices on a computer network is a sequence of connected computing devices that begins at the sender and ends at the receiver
Study plan for the AP Exam
